Hunting for Typosquatters: How a Full .NET Domain List is Your First Line of Defense
You’ve seen it happen. A carefully crafted phishing email lands in an employee's inbox. The link looks legitimate—almost. It points to microsft-support.net instead of microsoft.com. The employee, busy and distracted, clicks. Game over. In the world of cybersecurity and brand protection, the battlefield is expanding at an exponential rate, and one of the oldest, most effective attack vectors remains frustratingly potent: typosquatting.
We're not talking about niche, sophisticated zero-day exploits here. We're talking about the digital equivalent of a con artist wearing a slightly-off uniform. It's a game of deception, preying on human error, habit, and the sheer speed of modern business. For every brand that builds a decade of trust, there are a dozen opportunists ready to register a look-alike domain to siphon off that trust for malicious purposes.
This isn't just a problem for giants like Apple or Amazon. Any organization with a digital presence, from a regional bank to a promising SaaS startup, is a target. The damage isn't just financial; it's a deep erosion of customer trust, a logistical nightmare for support teams, and a potential compliance disaster. In this guide, we're going to move beyond the usual passive monitoring. We're going deep into the trenches of proactive threat hunting, using one of the most powerful yet underutilized tools in our arsenal: a complete, raw list of all registered .NET domains.
Table of Contents
- 1. The Hidden Threat of Brand Impersonation: Understanding Typosquatting
- 2. The Challenge: Why You Can't Protect Against What You Can't See
- 3. The Proactive Solution: Comprehensive Namespace Monitoring
- 4. A Practical Methodology for Detection: Scripting Your Hunt
- 5. Beyond Typosquatting: Expanding Your Threat Intelligence
- 6. Key Takeaways: Shifting from a Reactive to a Proactive Defense
1. The Hidden Threat of Brand Impersonation: Understanding Typosquatting
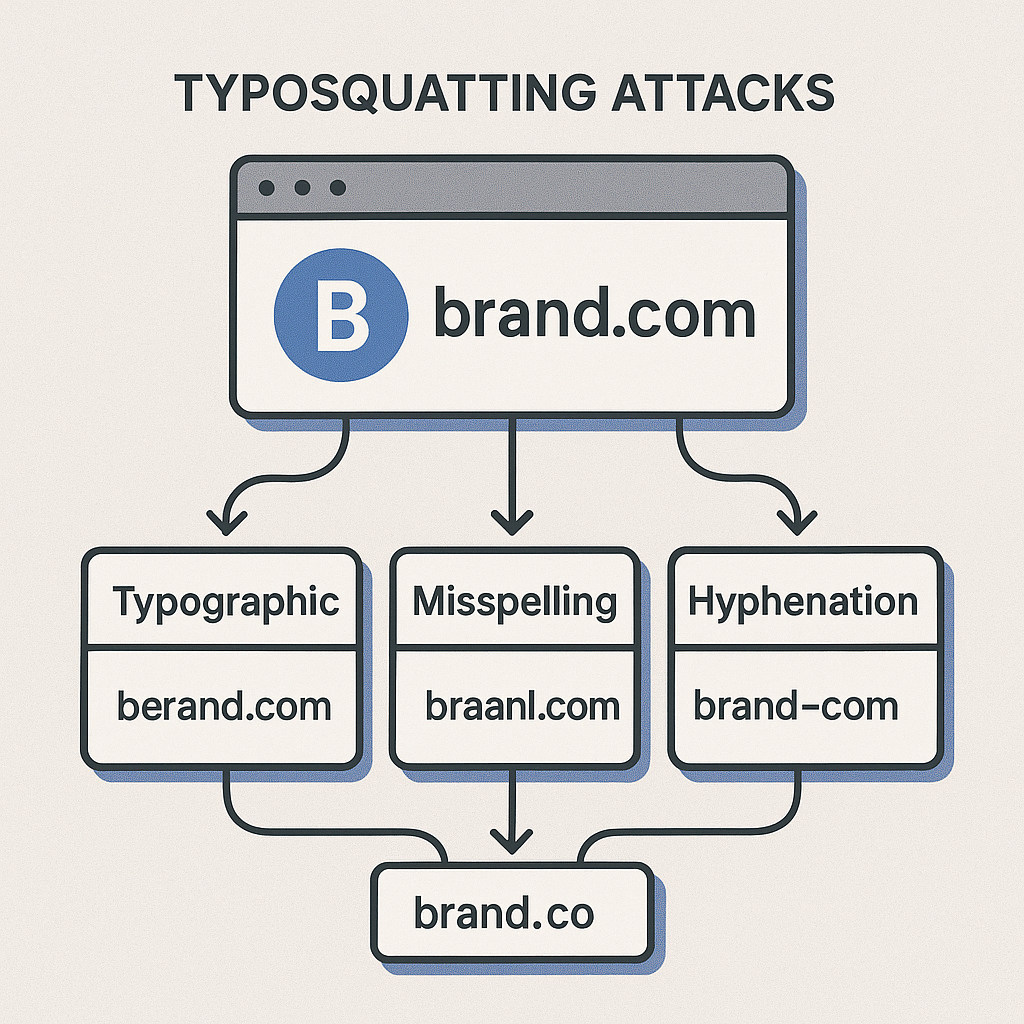
At its core, typosquatting, also known as URL hijacking, is a form of social engineering that targets users who incorrectly type a URL into their web browser or click a disguised link. The attacker registers a domain name that is a slight variation of a popular, trusted domain. The goal is to exploit common typographical errors.
Consider your own brand, let's say it's `securefinance.net`. A threat actor could register:
- Common misspellings: `securefinace.net` (missing 'n')
- Character omission: `secureinance.net` (missing 'f')
- Character permutation: `securefninace.net` (swapped 'n' and 'i')
- Different TLD: `securefinance.org` (often combined with other techniques)
- Homoglyphs: Using characters that look identical but are different (e.g., using a Cyrillic 'a' instead of a Latin 'a'). This is particularly insidious.
- Bitsquatting: A more advanced technique where an attacker registers a domain name that is one bit different from the target domain's binary representation, hoping to catch users whose computers flip a bit in memory.
Once they have control of this look-alike domain, the possibilities for misuse are vast:
- Phishing Campaigns: Creating a pixel-perfect copy of your login page to harvest user credentials. This is the most common use case.
- Malware Distribution: Prompting users to download a "required software update" or "security patch" that is actually ransomware or a keylogger.
- Monetization through Ads: Setting up a "parked" domain filled with ads, generating revenue from the misdirected traffic.
- Brand Slander: Creating a site to post false or damaging information about your brand, often called "gripe sites."
- Selling Counterfeit Goods: If you're an e-commerce brand, they can set up a fraudulent storefront.
The effectiveness of these attacks lies in their subtlety. An employee receiving an email from `it-support@myc0mpany.net` (with a zero instead of an 'o') might not notice the difference on a small mobile screen or during a busy workday. This is where brand damage begins.
2. The Challenge: Why You Can't Protect Against What You Can't See
So, the threat is clear. The logical next question from any CISO or brand manager is, "How do we monitor for this?" This is where most organizations hit a wall. Traditional methods are often inadequate for the scale and speed of the modern domain registration landscape.
- Google Alerts: You can set up alerts for your brand name, but they are notoriously slow. A malicious domain can be registered, used for a phishing campaign, and taken down long before it ever appears in a Google Alert. It's a lagging indicator, not a proactive tool.
- Manual Searching: Can you imagine tasking an analyst to manually search for hundreds of variations of your brand name every day? It's an impossible, soul-crushing task that is guaranteed to miss things.
- Commercial Brand Monitoring Services: These services can be effective but often come with a hefty price tag. More importantly, they often operate as a "black box." You get a report of potential infringements, but you don't own the underlying data. You can't run your own custom analytics, integrate it with other threat intelligence feeds, or pivot your search based on a new attack vector you've identified. You are limited by their dashboard and their methodology.
The fundamental problem with all these approaches is that they are reactive. You are waiting for a signal to appear on your radar. By then, the damage may already be done. To truly get ahead of the threat, you need to shift your perspective. You need to see the entire landscape—the entire map of the .NET namespace—and proactively hunt for threats within it.
"Security is a process, not a product. It's a continuous, dynamic effort of defense, detection, and response."
Schneier's point is critical here. Buying a service is buying a product. Building a capability is creating a process. To build a robust brand protection capability, you need foundational data.
3. The Proactive Solution: Comprehensive Namespace Monitoring
Imagine trying to find a single wanted person in a massive city without a map. You could wander the streets hoping to get lucky, or you could obtain a complete city map, overlay it with intelligence, and strategically deploy your resources. This is the difference between reactive monitoring and proactive threat hunting.
In our context, the "city map" is a complete, up-to-date list of every single registered domain within a specific Top-Level Domain (TLD), such as .NET. When you possess the full list, the power dynamic shifts entirely. You are no longer waiting for threats to announce themselves. You are actively scanning the entire population of domains for suspicious patterns that match your brand's signature.
Your security analysis is only as good as your data. To effectively hunt for potential threats across an entire TLD, you need a complete map of the territory. A full database of the .NET namespace is the critical first step. It provides the unfiltered, comprehensive dataset that allows for deep, customized analysis far beyond the capabilities of public search engines or basic monitoring tools.
We provide a regularly updated list, specifically curated for security professionals and brand managers, which serves as the foundational layer for this proactive strategy. This isn't just a list; it's a strategic asset.
Ready to build your proactive defense?
Acquire the complete, up-to-date .NET domain database and start hunting today.
Get the Full .NET Domain List
With this data in hand, you're no longer playing defense. You're on the offense.
4. A Practical Methodology for Detection: Scripting Your Hunt
Owning the data is the first step. The next is knowing how to use it. We'll walk through a simple yet powerful methodology using Python, the de facto language for data analysis and cybersecurity scripting. This approach is flexible, scalable, and entirely under your control.
4.1. Setting Up Your Environment: Python and Pandas
If you don't already have a Python environment set up, here's a quick guide. We'll use the `pandas` library, which is an incredibly powerful tool for handling large datasets like a domain list.
Step 1: Install Python
If you're on Linux or macOS, you likely already have Python installed. You can check by opening a terminal and typing `python3 --version`. If not, or if you're on Windows, head to the official Python website.
➡️ Download Python: https://www.python.org/downloads/
During installation on Windows, make sure to check the box that says "Add Python to PATH". This will make it easier to run scripts from the command line.
Step 2: Install Pandas
With Python installed, you can use its package manager, `pip`, to install the pandas library. Open your terminal or Command Prompt and run:
pip install pandas
This command downloads and installs the library and its dependencies. That's it. Your environment is now ready for analysis.
4.2. The Core Script: Generating and Finding Variations
Now for the fun part. We will write a Python script that takes your brand name, generates a list of potential typosquatting variations, and then searches for those variations in the full `.NET` domain list.
Let's assume you've acquired the `.NET` domain list from Webtrackly and saved it as a simple text file named `net_domains.txt`, with one domain per line.
Here is the full script. We'll break down what each part does below.
import pandas as pd
import time
def generate_variations(brand_name):
"""
Generates a comprehensive set of potential typosquatting variations for a given brand name.
"""
variations = set()
n = len(brand_name)
# 1. Omission (character removal)
for i in range(n):
variations.add(brand_name[:i] + brand_name[i+1:])
# 2. Insertion (character addition)
alphabet = 'abcdefghijklmnopqrstuvwxyz0123456789'
for i in range(n + 1):
for char in alphabet:
variations.add(brand_name[:i] + char + brand_name[i:])
# 3. Transposition (adjacent character swap)
for i in range(n - 1):
variations.add(brand_name[:i] + brand_name[i+1] + brand_name[i] + brand_name[i+2:])
# 4. Substitution (character replacement)
for i in range(n):
for char in alphabet:
if brand_name[i] != char:
variations.add(brand_name[:i] + char + brand_name[i+1:])
# 5. Homoglyph-like substitutions (common ones)
homoglyphs = {'o': '0', 'l': '1', 'i': '1', 'e': '3', 'a': '4', 's': '5', 'g': '9'}
for char_to_replace, replacement in homoglyphs.items():
if char_to_replace in brand_name:
variations.add(brand_name.replace(char_to_replace, replacement, 1))
return variations
def main():
# --- Configuration ---
BRAND_NAME = "securefinance" # Use the core part of your domain, without .net
DOMAIN_LIST_FILE = "net_domains.txt" # The full .NET domain list file
OUTPUT_FILE = "potential_typosquatting_hits.csv"
# -------------------
print(f"[*] Starting typosquatting hunt for brand: '{BRAND_NAME}'")
# Step 1: Generate all possible variations
start_time = time.time()
print("[*] Generating potential typosquatting variations...")
potential_variations = generate_variations(BRAND_NAME)
duration = time.time() - start_time
print(f"[+] Generated {len(potential_variations)} unique variations in {duration:.2f} seconds.")
# Step 2: Load the full .NET domain list into a pandas DataFrame
start_time = time.time()
print(f"[*] Loading full .NET domain list from '{DOMAIN_LIST_FILE}'...")
try:
# Assuming the file has no header and the first column contains domains
df = pd.read_csv(DOMAIN_LIST_FILE, header=None, names=['domain'])
# Strip the .net suffix to match against our brand name variations
df['name'] = df['domain'].str.replace('.net', '', regex=False)
duration = time.time() - start_time
print(f"[+] Loaded {len(df)} domains in {duration:.2f} seconds.")
except FileNotFoundError:
print(f"[!] ERROR: Domain list file not found at '{DOMAIN_LIST_FILE}'. Please check the path.")
return
# Step 3: Find matches
start_time = time.time()
print("[*] Searching for matches in the domain list. This may take a moment...")
# Convert the set of variations to a list for pandas isin() method
variations_list = list(potential_variations)
# Find all rows where the 'name' column is in our list of variations
hits_df = df[df['name'].isin(variations_list)]
duration = time.time() - start_time
print(f"[+] Search complete. Found {len(hits_df)} potential hits in {duration:.2f} seconds.")
# Step 4: Save the results
if not hits_df.empty:
hits_df.to_csv(OUTPUT_FILE, index=False)
print(f"[+] Results saved to '{OUTPUT_FILE}'. Please review this file for potential threats.")
else:
print("[*] No direct typosquatting matches found based on the generated variations. Your brand appears clear for now.")
if __name__ == "__main__":
main()
Breaking Down the Script:
generate_variations(brand_name): This is the engine of our detection. It takes your core brand name (e.g., "securefinance") and systematically creates a large set of possible typos by adding, removing, swapping, and replacing characters. It uses a `set` to automatically handle duplicate variations.- Configuration: At the top of the `main()` function, you can easily set your brand name and the filename of your domain list.
- Loading Data: The script uses `pandas.read_csv` to load the millions of domains from your `.NET` list into memory efficiently. It then strips the `.net` suffix from each domain so we can compare it directly with our generated brand variations.
- Finding Matches: This is the most crucial part. We use the powerful `isin()` method from pandas. It checks every single domain name in our list against our huge set of generated variations. This is incredibly fast and optimized, far more efficient than looping through the list manually.
- Saving Results: If any matches are found, they are saved to a clean CSV file (`potential_typosquatting_hits.csv`) for you to review.
4.3. Running the Analysis and Interpreting the Results
To run the script:
- Save the code above as a file, for example, `hunt.py`.
- Place it in the same directory as your `net_domains.txt` file.
- Open your terminal or Command Prompt, navigate to that directory, and run the command: `python hunt.py`
The script will print its progress. When it's done, you'll have a CSV file. This file is your first intelligence report. It's a list of domains registered in the .NET namespace that are typographical variations of your brand. Not every result will be malicious. Some might be legitimately registered by other entities for non-malicious reasons. But every single domain on that list warrants investigation.
Your next steps as an analyst would be to:
- Perform DNS lookups: Do these domains have active A or MX records? An active MX record is a strong indicator of a planned phishing campaign.
- Check for live websites: Use a tool like `eyewitness` or simply visit the sites (in a safe, sandboxed environment!) to see what content is being hosted.
- Review WHOIS data: While often redacted, sometimes WHOIS data can reveal information about the registrant.
This simple script, powered by a complete domain list, has just transformed your defensive posture from passive to active.
5. Beyond Typosquatting: Expanding Your Threat Intelligence
A full .NET domain list is not a one-trick pony. While hunting for direct typos is a powerful first step, the dataset can be leveraged for much broader threat intelligence and brand protection activities.
5.1. Combosquatting and Keyword Squatting
Combosquatting is arguably more common and dangerous than typosquatting. Instead of altering your brand name, an attacker combines it with keywords that imply trust or urgency. For a brand like `securefinance`, this could look like:
- `securefinance-login.net`
- `support-securefinance.net`
- `securefinance-portal.net`
- `securefinancesecure.net`
You can easily adapt the Python script to search for these patterns. Instead of generating variations, you would create a list of suspicious keywords (`login`, `support`, `portal`, `secure`, `account`, `verify`) and search the domain list for any domain that contains both your brand name and one of these keywords.
5.2. Brandjacking and Gripe Sites
This involves monitoring for domains that use your brand name to host negative content. While a domain like `securefinancesucks.net` might seem juvenile, it can rank in search engines and cause significant reputational damage. By having the full list, you can search for your brand name combined with negative keywords (`sucks`, `scam`, `fraud`, `boycott`) and identify these sites the moment they are registered, allowing your legal or PR team to act quickly.
5.3. Uncovering Malicious Infrastructure and C2 Servers
This is a more advanced use case for cybersecurity teams. Many malware families use Domain Generation Algorithms (DGAs) to create a large number of domains for their command-and-control (C2) servers. These algorithms often produce domains that look random (e.g., `asdfhjkweury.net`).
By having a full list of all registered `.NET` domains, security researchers can:
- Hunt for DGA patterns: Run analyses on the domain list to find clusters of domains with high entropy (randomness) that were registered around the same time.
- - Correlate with known threats: If a specific DGA pattern is identified by the security community, you can instantly scan your complete .NET list to see how many domains matching that pattern exist, effectively mapping out a piece of a botnet's infrastructure.
This level of analysis is simply impossible without the complete, raw data.
6. Key Takeaways: Shifting from a Reactive to a Proactive Defense
Throughout this guide, we've moved from understanding the basic threat of typosquatting to building a tangible, technical capability to combat it. The journey has taught us several key lessons:
- Passive defense is insufficient. Waiting for alerts or relying on black-box services means you're always one step behind the attackers. The modern threat landscape demands a proactive, intelligence-led approach.
- Foundational data is a strategic asset. Owning a complete list of a TLD's domains, like the `.NET` namespace, is the equivalent of having a high-resolution map of the entire battlefield. It is the ground truth upon which all further analysis is built.
- Simple tools can be incredibly powerful. With a foundational dataset and a simple Python script, any organization can build a sophisticated threat-hunting capability that is customized to their specific brand and risk profile.
- The value extends far beyond one use case. The same dataset used to find typosquatters can be used to uncover brandjacking, combosquatting, and even elements of global malware campaigns, providing immense return on investment for your security and brand protection programs.
You no longer have to wonder what's out there. By acquiring the complete `.NET` domain list and applying the methodologies we've discussed, you can actively search for, identify, and neutralize threats before they impact your customers, your reputation, and your bottom line. You can finally turn your defense from a reactive scramble into a proactive hunt.